Data Integrity and Security - US Chamber
Assume breach. It might be one of the most memorable pieces of cyber risk advice following the December 2020 discovery of an ongoing supply chain attack by a sophisticated threat actor, likely Russian in origin. If you are running these software versions, assume breach and hunt for adversarial behavior. Full stop. From the Security Teams to Chief Information Security Officers, we know that the worries and concerns of significant business disruption from a cyberattack are on the minds of many. But there is a better way for organizations to manage security. That approach is zero trust.
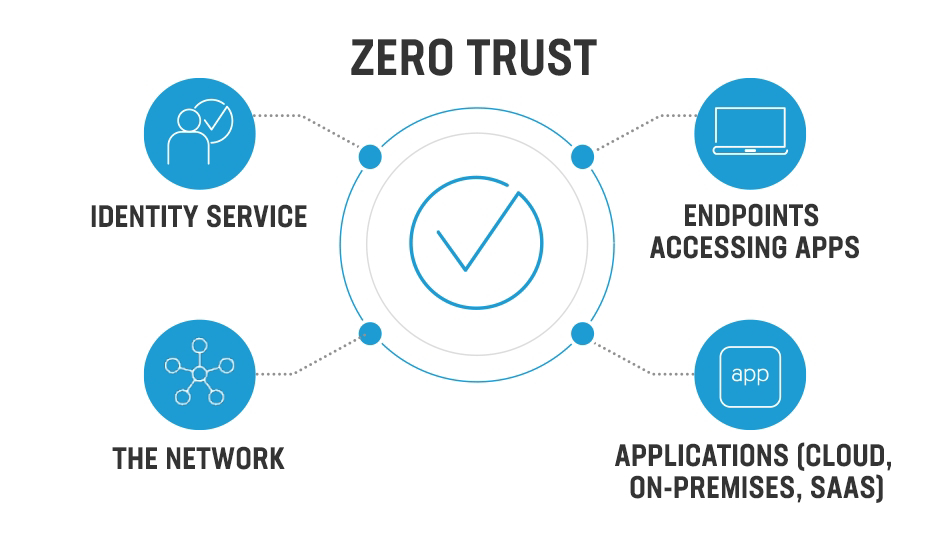
While the concepts of zero trust are not new, shifting away from trusted, firewalled, or castled networks is unknown to most enterprises. Many organizations are struggling to integrate these concepts in an information technology modernization strategy focused on security. Zero trust architectures assume that malicious actors are both within and outside the enterprise and that security teams need to validate the connections between every user, device, application, and dataset. In addition, organizations will migrate operations to the cloud and employ automated endpoint detection and response (EDR) capabilities. Cloud migration increases employee productivity by allowing secure connections from anywhere, from any device, while EDR technologies reduce potential business disruption by accelerating detection and response to threats.
In this panel discussion, our experts will talk about strategies to expedite the adoption of zero-trust architectures. While they will not cover the waterfront, panelists will focus on the highest value starting points for organizations to mature their zero-trust architecture (ZTA) maturity. The conversation will focus on identity, devices, networks, applications, and data as the foundational pillars of ZTA.
In a Nutshell :
Cybersecurity & Adv Cyber Threat Intel Research.
Mobile OS Hardening.
CyberSec Software & Platform Reviews.
Content Creation.
CMS LMS WebDev.
Convergence.
Diving Deep into incredible Research on CyberSec.
Cloud Archives.
Defense Grade Security Intelligence,Awareness,Forecasts,Strategy.
Research and Reports.
Simplifying Complex Pieces of Incredible Intel.
CyberSec Trends. Vulnerability Statistics.
US DOD Enterprise Security.
Email Threat Analysis.
Data Breach Industry Forecasts.
UK National Cybersecurity Reports.
Adversary Threat Hunting.
Protecting Digital Assets.
Advanced Persistent Threat Analysis (APT)
CyberCrime Modus Operandi and Statistics.
Nation State Security Trends.
National CyberPower Reports.
Age of Cyber Warfare.
Research reports on Advanced Cyberdefense Threat Intelligence by US Department of Defense , US Navy , National Cybersecurity Alliance ,US Cyber Command , NSA , FBI , US Department of Homeland Security DHS , CrowdStrike , Edgescan etc.
Lightning Fast Cybersecurity updates in real time.
https://flipboard.com/@easytech4all/cybersecurity-6tbejh5oz
Follow Blog for work in progress updates on R&D
https://easytech4all.net/author/easytechonline/

Comments
Post a Comment