Worldwide Cyber Threat Landscape
Role of AI and CyberDefense Threat Intelligence in Military Defense Industrial Complex. Future Projection Analysis based on Current Trends. By Easytech4all.net
- The Worlds largest Industry is the Military Industrial Complex.
- Pacifism and Peace undoubtedly being the most desired outcome of any diplomacy..still continue to elude humanity.
- The World is becoming heavily Militarised after the Advent of Smart Technologies. Regional Conflicts for scarce resources are erupting at a rapid pace. World War 3 may not be a distant Dream now.
- Medical Practitioners and AI Cyberdefense Threat Intelligence Professionals cast the most significant impact on the Military Industrial Complex.
- Medical Practitioners play an important role during Full scale Military Kinetic War and Conflagration. Microbiologists and Virologists play an important role in BioWarfare.
- As far as AI Engineers are concerned all Smart Defense systems have huge potential for innovation. From Facial and object Recognition to Missile cum Aircraft Smart Navigation systems. AI impacts everywhere. Military Robotics by DARPA and Boston Dynamics is a popular example here. Combat Drones are the smartest weapons in the Military Arsenal that determine the outcome of most battles today. They are Low Cost AI flying Machines when compared to 5th Generation Fighter Aircrafts.
Elon Musk recently said that the era of Fighter Jets has passed . The Future belongs to Combat Drones. And if you thought that Hollywood’s Iron Man was a figment of imagination..think again because you haven’t seen the Royal Marines yet. Scifi Hollywood and the Gaming industry is nothing but future Projection and Analysis. - Finally CyberDefense Threat Intelligence plays an undeniable role in Full Spectrum Military Cyberspace operations. Cyber is the 5th War Domain after Land , Air , Sea and Space. But Cyber Alone affects all the other domains. Today CyberAttacks can be as deadly as Military Kinetic operations precisely why NATO has brought Article 5 on the table for any APT action on Allied Nations. Meaning that NATO will consider a Cyber Attack on any ally as an attack on all and respond with Military Kinetic Force on the Adversary. Defending the Military , Energy , Avaition , Hospital , Government and Nuclear Critical infrastructure is of great importance today.
A threat landscape (also called a threat environment) is. a collection of threats in a particular domain or context, with information on identified vulnerable assets, threats, risks, threat actors and observed trends.”
5 biggest cybersecurity threats
- Social engineering. …
- Ransomware. …
- DDoS attacks. …
- Third party software. …
- Cloud computing vulnerabilities.
A cyber or cybersecurity threat is a malicious act that seeks to damage data, steal data, or disrupt digital life in general. Cyber attacks include threats like computer viruses, data breaches, and Denial of Service (DoS) attacks.
Differentiating cyber attacks generational wise was something which the security experts from CheckPoint introduced to the world. In their cyber threat dictionary, first generation cyber attacks were virus threats on floppy discs that would infect a single computer. The 2nd generation attacks were those which infected networked computers with viruses. 3rd generation attacks were browser-based cyber threats. 4th Generation of attacks was Polymorphic attacks where the virus has the ability to change its traits based on the system and the environment which it is trying to intercept. And as per the CheckPoint analysis, the 5Th generation attacks are those which take place so fast that preventive- that too proactive measures are required to counter them- rather than reactive measures.
“In today’s world, it’s a fact that our mobile phones contain more info than our desktops. But the manufacturers or the OS makers aren’t focusing much on security making them vulnerable to cyber attacks”, said Jarvis.
Highlighting attacks which topped the year 2018, Jarvis said that online attacks and Cryptocurrency mining attacks followed by Banking Trojans, phishing and other forms of malware were mostly analyzed by their company in last year. Also, Ransomware developers became lethal as they started to use cryptocurrency to keep their activities concealed from law enforcement agencies.
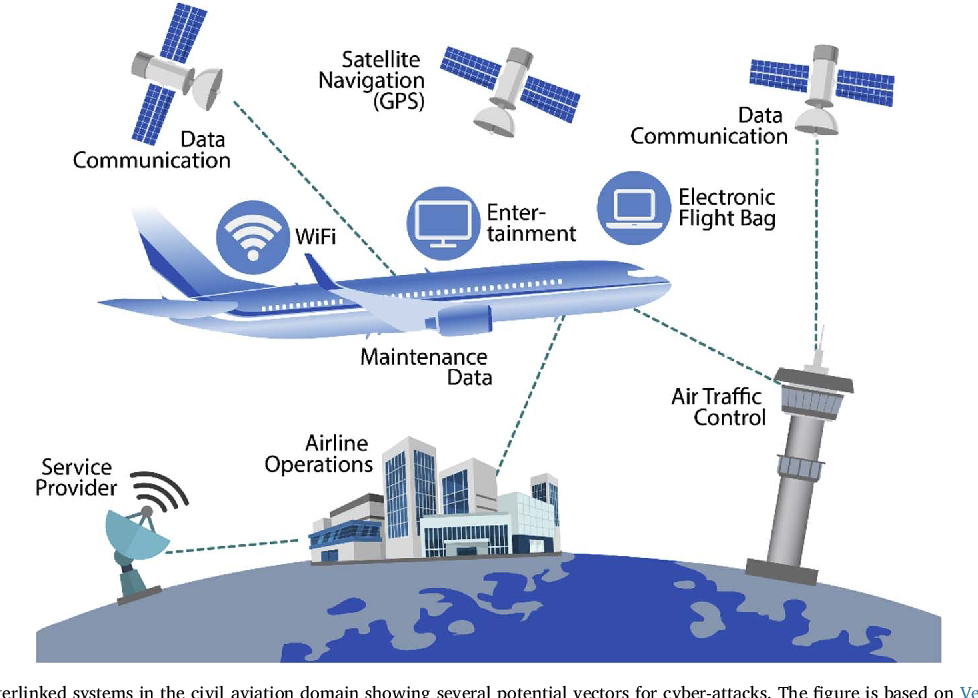
Birds Eye View of Cyber Threat Landscape

Comments
Post a Comment