Global Cyber Intelligence - Consecrated
Global Cyber Intelligence Consecrated . This Video Presentation is rededicated to the International Cyber Defense Umbrella comprising of Military Alliance Cyber Commands , Government and Federal Cyber Defense Agencies , Private CTI Defense Corporations , Security Operations Centre , Computer Emergency Response Teams , Transnational Independent Cyber Threat Intelligence Analysts & Specialists.
Youtube Video Presentation
KEY HIGHLIGHTS -
UN , US , NATO , INDIA , Federal Security Agencies , Military Cyber Force and Commands , Private CTI Agencies and Corporations.
# Two invaluable book recommendations from UN and suggestions to UN . My recent reads .
"The Basic facts about UN" is a mini encyclopaedia. Not just about UN but Copernican World Events and Crisis/Conflict response at the Macro Level including the development and progress of ICT's and the ICT task force. The historical significance and evolution on a chronological linear timeline. Also quite significant was the section on Peaceful use of outer space - Relevant Treaties and Agreements. UNISPACE conferences , cooperation with European Space Agency (ESA) , NASA , International Astronautical Federation (IAF) , Committee on Earth observation satellites (CEOS) , Committee on Space Research (COSPAR) etc.
The other Book uncommon opportunities - Agenda for Peace and Equitable development
The Report of the International Commission on Peace and Food by International Center for Peace and Development USA and M.S. Swaminathan Research Foundation Chennai India .
Highlights are the sections on the "Peace Imperative" - Information Superhighways , War as an instrument of Policy , Nuclear Weapons (START 1 , START 2 , NPT , CTBT , Ballistic Missiles) , Confidential Studies by NATO , Cooperative Security, MAD doctrine , World Army Proposition and Hypothesis etc . Alacritous rise of India and China in the Global Order and what made it possible.
# US Cyber Policy for Deterrence. Executive Order 14028 Improving the Nation's cybersecurity. This EO Mandates endpoint protection , defining logging requirements , implementing audit logging in a unified way and enhancing the capabilities to provide further insight into system and account actions. The EO responds to an increase in Cyberattacks that use ransomware to cripple critical infrastructure components related to National Security and the public . Enhancing existing information assurance security controls as a part of a Risk management framework is a suitable mechanism to facilitate compliance and justify funding based on these Presidential requirements.
White House Cyber Physical Resilience Initiative (ISSA SIG) - Cyber Resilience refers to the ability to protect electronic data and systems from cyberattacks as well as to resume business operations quickly in case of a successful attack. In times of increasing damage and sophistication of attacks it is of paramount importance to develop critical cyber resilience capabilities in each organisation. Yet cyber resilience is currently understood differently by various organisations despite the fact that NIST had published clear guidelines(800-160) then followed by other valuable publications and initiatives from MITRE , CERT -US , CISA etc.
# NATO CCDCOE Locked Shields Livefire Exercise 2023 - a unique international Cyberdefence Exercise offering the most complex technical live fire challenge in the World. From a Strategic perspective the exercise offers training and practice in effective decision making and crisis coordination when facing large scale cyber attacks targeting the critical sectors and it's infrastructure. NATO Cyber Commanders Handbook 2.0 at stakeholders meeting in Tallinn Estonia - leveraging a cooperative approach for Cyber Defence.
# India's meteoric rise in United Nations Specialised Agency for Information and Communication Technologies - International Telecommunication Union (ITU) ranking for everything Cybersec . Ranked at 10th from the 47th Spot with an overall Score of 97.49. 4th Spot in Asia Pacific Region.
USA and UK ranked First and Second respectively. Saudi Arabia and Estonia was ranked third. South Korea , Singapore , Spain shared the fourth spot . Russia , UAE , Malaysia shared the Fifth Spot . Lithuania came in sixth followed by Japan , Canada , France at seventh , eight and ninth respectively.
Also 3 Indian Leaders have been named in Global Hall of Fame report that identified "CLOUD SECURITY AS THE BIGGEST CHALLENGE" - Indian Govt once said that they want to make INDIA the Global hub for Cybersecurity. And India is indeed making some good progress in that much needed direction . As a fast growing "World Class Digital Payment Ecosystem" economy - Cybersecurity and Cyber Resiliency become of paramount importance mechanically.
Open Source Software is India's inherent Strength . A Quick analysis of the Internet and YouTube will reveal India's talent in Open Source OS Linux distros - Ubuntu , Fedora , Kali Linux , Elementary OS , Debian etc . DIY's and How 2 Do's across the length and breadth of the Internet unveil this hidden untapped and unorganised skill set that needs to be developed and promoted further . The Beauty of OSS are the following.
1. Right to use study change distribute the software and its source code to anyone for any purpose.
2. Development in Collaborative Public Manner.
3. Examine the Code thereby facilitating public trust in the Software.
Linux has the largest installed base of all general purpose operating systems ( including AOSP and ChromeOS) . From running the terminals at the International Space Station to some of the fastest supercomputers..OSS is everywhere.
The Chromebook, which runs the Linux kernel-based ChromeOS, dominates the US K–12 education market and represents nearly 20 percent of sub-$300 notebook sales in the US. Linux is the leading operating system on servers (over 96.4% of the top 1 million web servers' operating systems are Linux), leads other big iron systems such as mainframe computers, and is the only OS used on TOP500 supercomputers (since November 2017, having gradually eliminated all competitors).
Linux also runs on embedded systems, i.e. devices whose operating system is typically built into the firmware and is highly tailored to the system. This includes routers, automation controls, smart home devices, video game consoles, televisions (Samsung and LG Smart TVs use Tizen and WebOS, respectively), automobiles (Tesla, Audi, Mercedes-Benz, Hyundai, and Toyota all rely on Linux), spacecraft (Falcon 9's and Dragon 2's avionics use a customized version
More Snapshots in the above video presentation.
# Future of the Intelligence Community Workforce - Enabling a Secure Hybrid Work Environment - CIA and MITRE Corp.
# US Cert (Computer Emergency Response Teams) , Cybersecurity and Infrastructure Security Agency (CISA) National Security Agency (NSA) Events .
# Intelligence and National Security Alliance (INSA) and ISSA (Information Systems Security Association) Brainstorms Webinars Seminars .
#. EU Cyber Defence Innovation Program.
# European Cyber Agora.
# National Cyber Strategies to Defend Critical Infrastructure.
# Global Annual Cybersecurity Summits and National Cybersecurity Alliance endeavours.
# UKCSA UKSec - Challenges faced by Governments and International Law Enforcement.
#. Cybersecurity Projections and Predictions.
# Cyber Task Force - FBI Criminal Cyber Squad .
# Cyber World Congress - 24 hr Virtual Events.
#. Cyber Threat Intelligence Talks.
#. CyberAI and its impact on OSINT.
# Cyber Intelligence Units Quarterly Updates (Infoblox)
# CYBERWARFARE PREPAREDNESS by Allen Ari Dziwa.
# Military Cyber Commands and Cyber Force (SoC- Trident Jaguar)
# Assessing the risk and Protecting the Supply Chain.
#. Podcast on Cyberweapons.
#. Future of Cybersecurity and Risk Analysis.
# Cyber Threat Intelligence and Incident Response.
# Cybersecurity Advanced Persistent threat Defenders Overview.
#. Virtual Intelligent Automation Exchange - Director of AI Defense Intelligence Agency (DIA)
#. Small Business National Security Showcase (Directorate of Digital Innovation CIA)
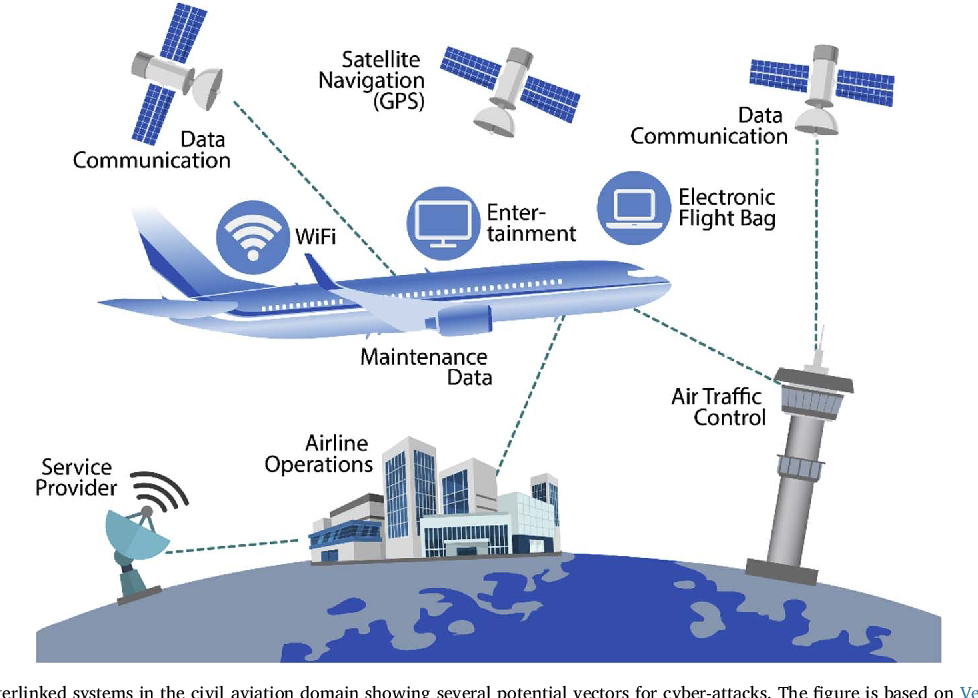
#. CISO perspective - Delta Airlines.
#. Cyber Strategies for a World at War (Open Source Aggregation and Analysis).
#. WEF and INTERPOLs Global Risk Annual Assessments and SOC - Cyber Ploygon.
#Google Cloud Security talks and threat Analysis Group.
#Digital Risk Management e-learning platform for mediators. UN DPPA and Cyberpeace Institute.
1PowerCyber @ Easytech4all CTI Research & Analysis consultancy focuses it's energies on Military Cyber Commands and Global Federal Agencies CTI reports , webinars , brainstorms , bright talks by global industry and Agency experts to build a threat Intel knowledge pool . The Cyber Threat Intel Knowledge pool in turn takes shape of mindmaps , infographics and video content presentations to be used for Blogs , Digital Magazines , Newsletters and CMS .
This Knowledge pool also facilitates analysis and benchmarking of EDR/NDR , Siem , SOAR solutions available for different ecosystems . This coupled with OSINT research conducted through different search engine Algorithms facilitates proactive Cyber Threat Intelligence Projections incorporating various Geopolitical , Strategic and Policy inputs. Eventually this threat Intel gets included on Collaborative CMS & services integration platform.
Cyber Strategic Communication based on OSINT and Global Cyber Policy Analysis also remains an area of Major interest as it is indispensable for future Cyber threat projections.
OS Hardening - Mapping Desktop / Mobile OS and Application Security with every successive firmware and security patch is continuous work in progress at the Threat Intel Research Consultancy.
This Video Presentation is a succinct snapshot of some Preliminary and detailed experience with Global Cyber Intelligence Think Tanks , Organizations and Associations .
From Researching Analysing Cybersecurity and CTI Products/Services to functioning as a Cyber Threat Intel Provider for Governments , Global Agencies and CTI Organisations. The Scope for Transnational Cyber Alliance remains stupendous.
1Power Easytech4all Cyber threat Intelligence Solution primarily relies on the Cyber Prudence and Strategic Insights of Global Experts from UN Cyber Policy Assessments and Debates on ICT's , White House Cyber Policy EO's , Risk Assessments , White House Cyber Resilience Initiatives through various organisational SIGs etc . Also ISSA , INSA ,NATO , UNIDIR , European Defence Agency (EDA) , National Security Agency (NSA) , Cybersecurity and Infrastructure Security Agency (CISA ), Federal Bureau of Investigation (FBI) , World Economic Forums (WEF) Annual Critical Risk Assessments and Cyber Polygons (SOCs) in addition to Pvt Agency Security Operations Centers findings plus CTI analysis.
They are the Cyber beacons for the World shaping Global Cyber Policy and Cyber Deterrence Countermeasures plus standards .
1PowerCyber @ easytech4all.net
https://1powercyber.substack.com
https://1powercyber.blogspot.com
https://easytech4all.tumblr.com
https://linktr.ee/1powercyber


Comments
Post a Comment